DevOps and DevSecOps both use automation and continuous processes for collaborative development, but the DevSecOps aspect focuses on automating security tasks within the DevOps workflow. We'll show you a set of tools that will be useful to have better security integration and conscience within your repositories.
This quick tutorial will show you how to get all sources from a repo and scan them with Sast-scan tool to spot secrets, tokens, bad libraries, sensitive information or security weaknesses in your repo.
Ghorg
First, we need to get the sources from our repo. Ghorg is a useful tool to get everything from a repository. It will quickly clone all of your orgs and repos into a single directory.
|
Get all the repos from a specific group
If you would like to get the sources from a specific group, you just have to pass the group's name in your command. Example here with the "security" group.
|
Find and report secrets, bad security configurations, dependencies or sensitive data
After getting everything we need, we now have to scan the sources.
Sast-scan
Sast-scan is a free and open-source security tool designed for modern DevOps teams. It utilizes an integrated multi-scanner approach to identify a wide range of security vulnerabilities in both your application and infrastructure code, all in a single, rapid scan, without requiring a remote server. Scan is specifically made for seamless integration into your workflow and includes useful features like automatic build interruption, baseline results, and comments summarizing pull requests. The Scan products are open-source and licensed under Apache-2.0.
Sast-scan has the following capabilities of language analytics
| Programming Language | Tools |
| ansible | ansible-lint |
| apex | pmd |
| arm | checkov |
| aws | checkov |
| bash | shellcheck |
| bom | cdxgen |
| credscan | gitleaks |
| depscan | dep-scan |
| dockerfile | checkov |
| go | gosec, staticcheck |
| groovy | find-sec-bugs |
| java | cdxgen, gradle, find-sec-bugs, pmd |
| jsp | pmd, find-sec-bugs |
| json | jq, jsondiff, jsonschema |
| kotlin | detekt, find-sec-bugs |
| scala | find-sec-bugs |
| kubernetes | checkov, kubesec, kube-score |
| nodejs | cdxgen, yarn, rush |
| php | psalm, phpstan (ide only) |
| plsql | pmd |
| python | cfg-scan (1), bandit, cdxgen |
| ruby | brakeman (2), dep-scan |
| rust | cdxgen |
| serverless | checkov |
| terraform | checkov, tfsec |
| Visual Force (vf) | pmd |
| Apache Velocity (vm) | pmd |
| yaml | yamllint |
| docker/container image | dep-scan |
It's possible to do the complete analysis of all your repositories but you might need better scopes isolation.
|
If you need to separate the bit more analysis scope, you can proceed by group/project with something like this
|
During the analysis, Sast-scan will display summarized info for each directory the scan is analyzing (and the plugins it will use). It will eventually directly show you the dependency scan results:

The analysis time depends on the content of your repo, but you should have results within a few minutes.
When the analysis is over, we can see that a "reports" directory has been added to the project and it contains html files with the analysis results.

In those files, you'll get infos about what has to be corrected. Here're 3 examples of things to correct
- Example 1: creds in a yaml file

- Example 2: vulnerabilities in the source
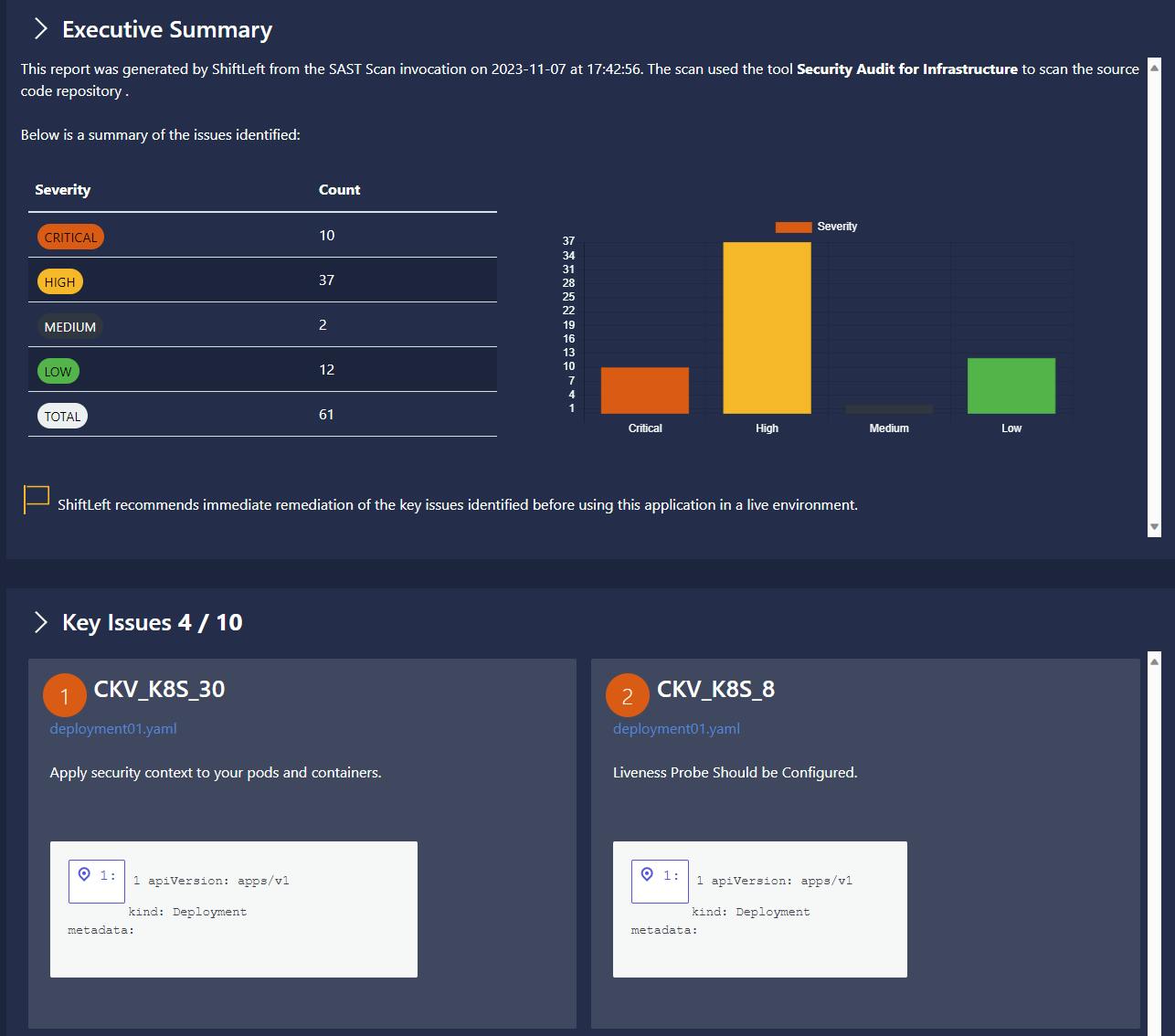
- Example 3: bad dependencies

If everything is correct, you will get this result page :
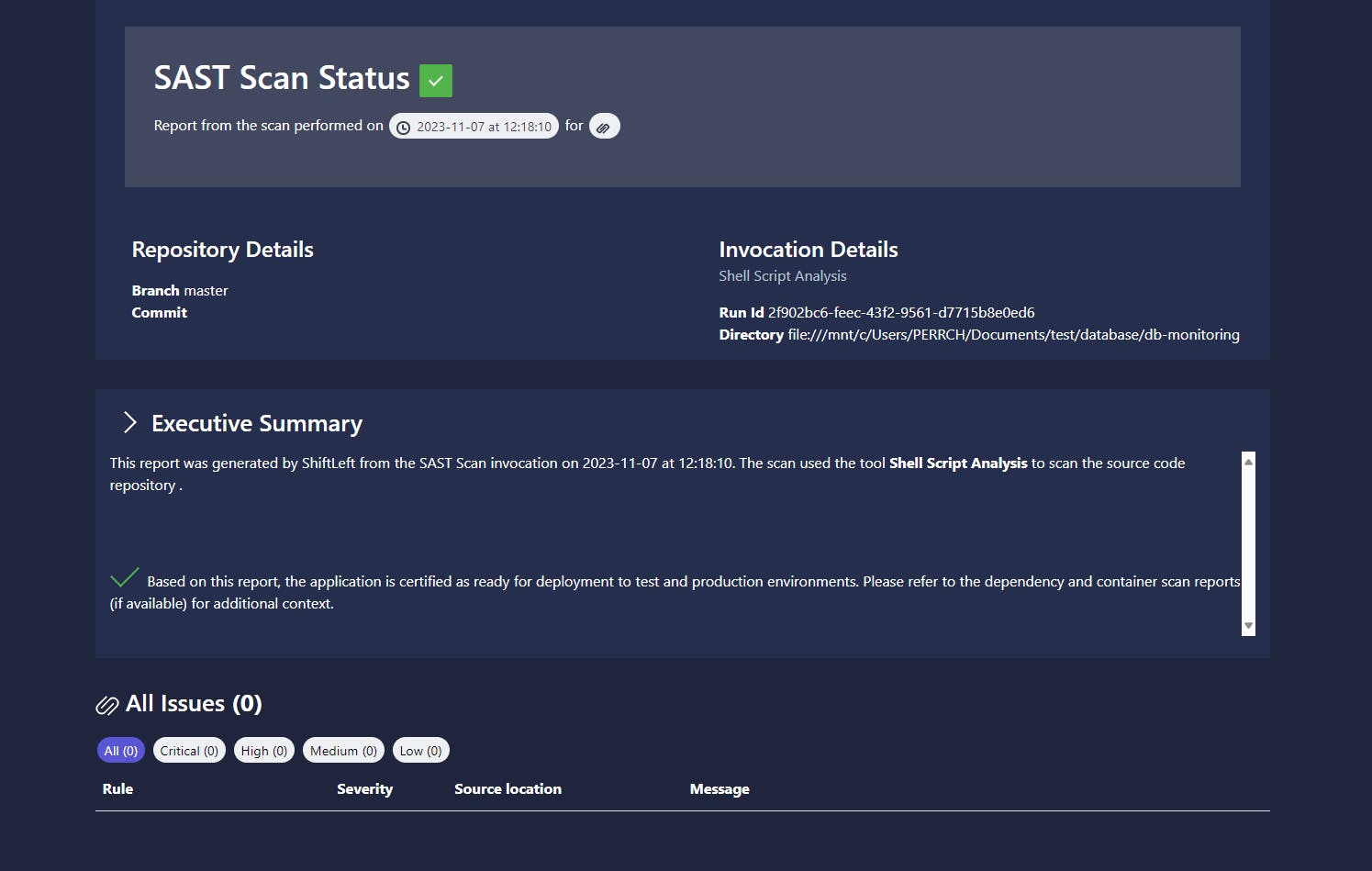
Perfect! You're now able to scan your repo for any security weakness and deploy your projects with the best security context for a better DevSecOps practicing !

